
No doubt. Cybersecurity is intimidating.
Working for the world's largest cybersecurity company, it's been a part of my world for decades and now you have the benefit of an expert in your back pocket.
It can sure feel intimidating to reach out to an expert, but you don't know what you don't know so if you have questions, others do, too.
Just think! You'll be helping me help many more people, just by asking. But, feel free to take a look below, because...
Here's Everything I Offer
I'm Speaking At
This Summit

INFORMATION


Security Alert - Whaling

On November 17, 2023, I posted about it being the start of the phishing season.
I’m going to update you on the latest round of attacks including what to do when it’s happening, what to do right now after reading this, and a few additional tips to help you keep yourself, family, and friends safer.
The attack category is Social Engineering Attack. So I’m going to start this with a little primer on these attacks.
Attack Type Communication Channel Target
Phishing Email All
Vishing Voice: often using VoIP All
Whaling Email and/or Voice Individual
Smishing Text Both
Social Engineering Social Media Both
How and Why:
Tactics: Impersonation, urgent action required, Threatening/Fear
End-Result: Personal information, Financial information
Most people have heard about phishing (the OG) and so they use it to describe any socially engineered attack.
Phishing and its voice counterpart target as many potential victims as possible. Usually for vishing, it’s a recording with a request to call a specific number.
Whaling targets a specific individual.
Smishing and Social Media SEs may target both.
Today, December 30, 2023, I’m going to talk about a specific whaling attack.
I’m seeing people I know posting about receiving a call from their “bank” with a live person who has a considerable amount of information that makes the call recipient believe it is legitimate. Now if you’re expecting a call from your extremely local bank because you called and left a message, you probably know exactly who is calling you back.
First thing to know: There’s a lot of data collected by legitimate data collectors and it’s for sale. There are also breaches occurring where the illegally acquired data is also sold.
Second thing to know: No bank or financial institution will cold call you via a live representative.
The best security practice most banks use is to leave a voice message, usually identifying the department (i.e. fraud) with the instruction to:
CALL THE NUMBER ON THE BACK OF YOUR BANKCARD/CREDIT CARD.
So, here’s what to do if it happens to you:
1️⃣ HANG UP - yup, cut them off right after they say the financial institution’s name, if possible.
2️⃣ CALL THAT NUMBER - Ask for the fraud unit and let them know there was a potential phishing/whaling attack.
3️⃣ GET A CASE # - If the bank unit opens a case.
4️⃣ CONTACT LOCAL POLICE - If you’ve gotten a case number.
So, here’s what to do right now after reading this post.
Login to either your bank app or directly online:
1️⃣ SET-UP NOTIFICATIONS - Set-up notifications for every bankcard transaction to be sent to your email account.
⏺️Purchases outside of physical merchant
(may show up as Card Used Online, by phone or by mail)
NOTE: depending on the bank, you may be able to set-up
physical purchase notifications
⏺️Direct Deposit Notice
⏺️Low Account Balance - You set the amount for this notification.
2️⃣ SET-UP MFA - Multifactor Authentication is the strongest account security.
3️⃣ CHECK FOR SECURITY RECOMMENDATIONS - then use them.

CEO Security Brief Waitlist
The CEO Security Brief is opening soon! Join the waitlist now to get an early-bird notification before it opens.
unAPPetizing:
What To Look For When App Updates Are Rotten Free - Coming Soon
Your mobile apps may start out passing Google's & Apple's stringent security vetting, but once downloaded, updates may not be safe.
JOIN THE WAITLIST
Get it now [Link]
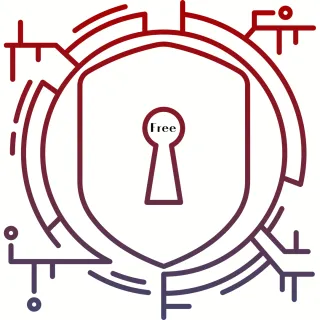
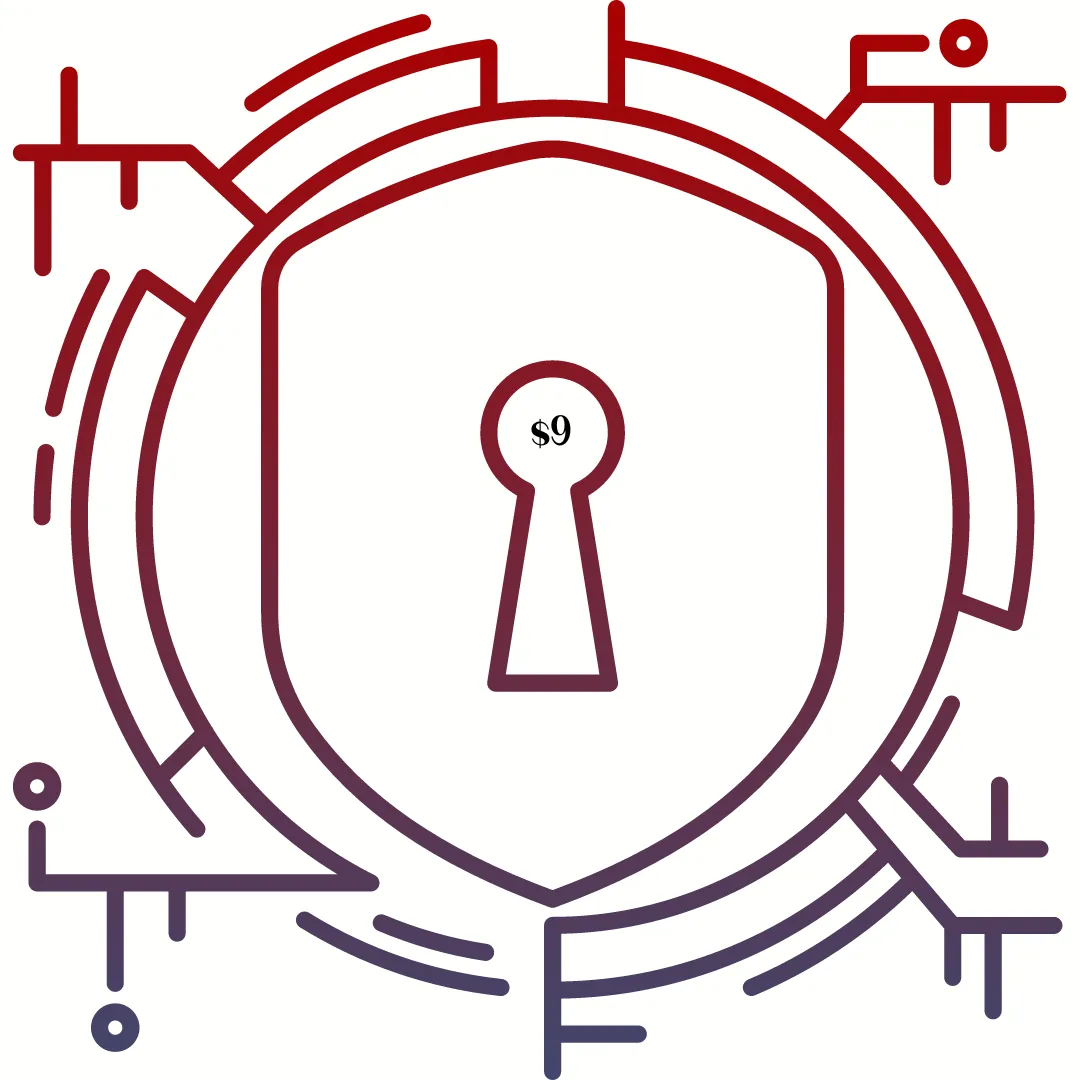
The Human Firewall: Strengthening Your Cybersecurity Mindset $9 - Coming Soon
Cybersecurity is intimidating, especially when you don't know what you don't know. In this mini-training, we'll cover some basic principles, definitions, methods, and tools to help you create your cybersecurity plans.
Join the Waitlist
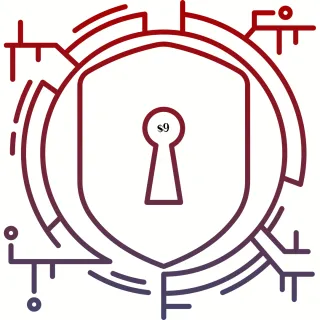
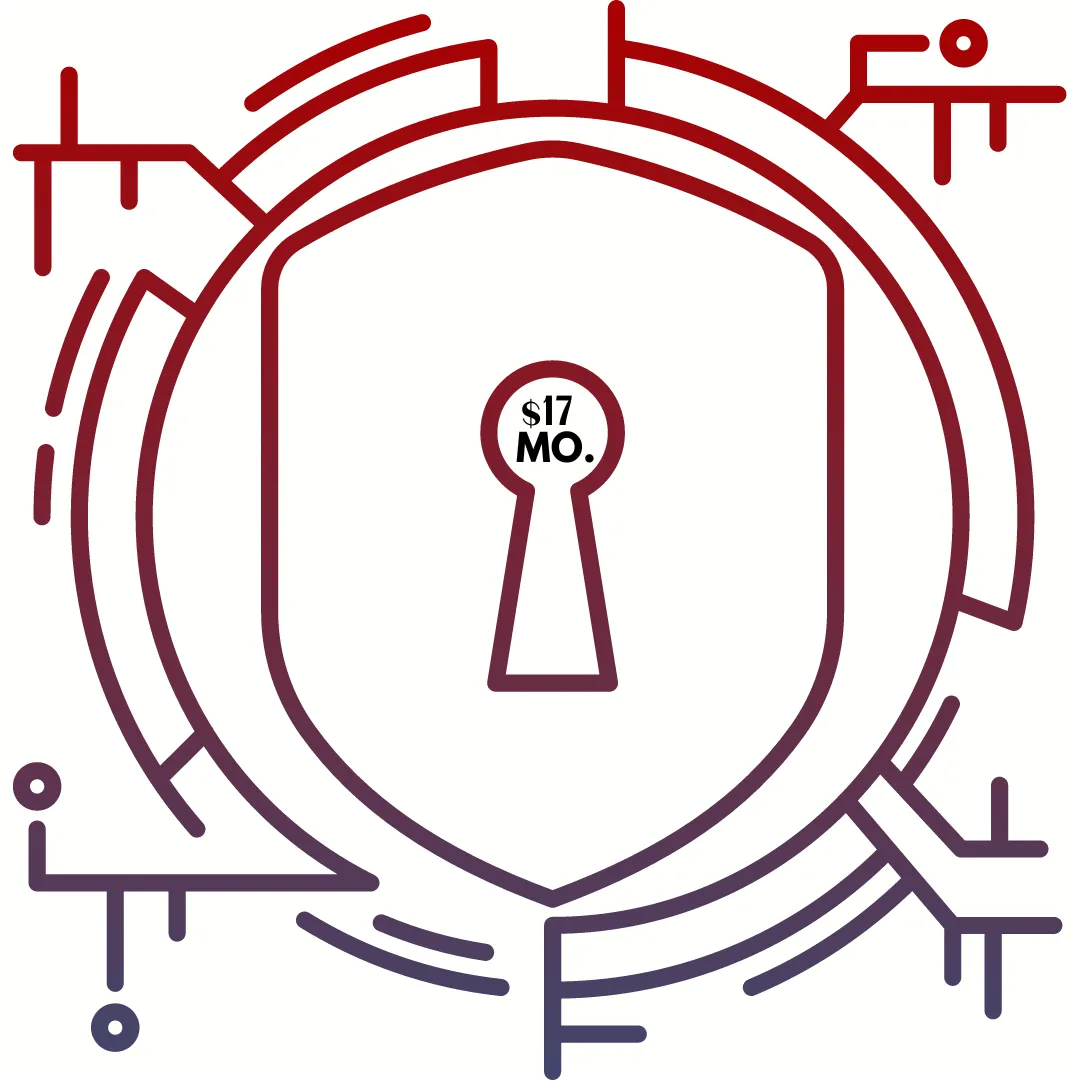
Alert & Secure - Curated Security News + Threat Alerts $9/mo.
Stay on top of the latest in the threat landscape with this weekly subscription newsletter. Get top recommended solutions, products, and strategies provided by cybersecurity experts from around the world. I do this for myself, friends and family. I can do this for you, too, so you don’t have to go down that cybersecurity rabbit hole.
Subscribe
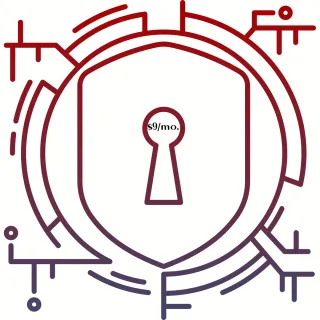
On-demand Workshop: Give Phishers The Phinger: Social Media Secured $197 - Coming Soon
A quick under 1 hour security training to secure your Facebook account while giving phishers the phinger.
Phlip off Phishers, Now [Link]
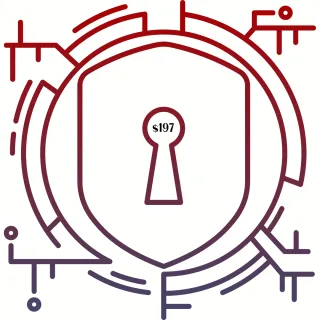
On-demand Workshop: Spy Ring: Is Your Smart Home Helping The Bad Guys? $197 - Coming Soon
Those smart devices and appliances that make things easier for you... also makes it easier for cybercriminals to gain access to your home network. Ask the casino in Vegas hacked through a fish tank with a remote monitoring system connected to the corporate network about the $billion heist.
Learn how to keep your Roomba in check, your Ring on your side, and your front door locked.
Become a WiFi Warrior [link]

On-Demand Workshop: Mobile Mayhem: Securing Your Business on the Go $197 - Coming Soon
Lorem ipsum dolor sit amet, consectetur adipisicing elit. Autem dolore, alias, numquam enim ab voluptate id quam harum ducimus cupiditate similique quisquam et deserunt, recusandae.

On-Demand Workshop: Lock and Locate: Securing Your Devices Against Theft - Android $197 - Coming Soon
Discover the art of device protection in this workshop focused on securing your Android smartphones, laptops, and tablets.
From enabling tracking features to setting up remote wipe capabilities, you'll learn how to keep your devices safe from physical theft with a bonus of helping the police nab the thief.
STOP. Thief! [link]

On-Demand Workshop: Lock and Locate: Securing Your Devices Against Theft - Apple $197 - Coming Soon
Discover the art of device protection in this workshop focused on securing your Android smartphones, laptops, and tablets.
From enabling tracking features to setting up remote wipe capabilities, you'll learn how to keep your devices safe from physical theft with a bonus of helping the police nab the thief.
STOP. Thief! [link]

Course: Back That Biz Up: Recover From Catastrophe and Restore Your Revenue - $297 - Coming Soon
A cyberattack can be catastrophic and having a Business Recovery Plan or Disaster Recovery Plan as a strategic guide — detailing the processes and timelines needed to restore your critical functions to pre-incident levels ASAP — can minimize the effects of the incident so you can continue to operate and quickly resume key operations.
Learn More [link]
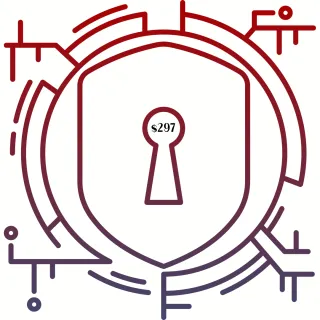
Course: Beyond Phish Phingers: Shielding Your Revenue Tools - $297 - Coming Soon
Go beyond Social Engineering Attacks with essential strategies, tools, and techniques to protect your business revenue tools, such as payment gateways, e-commerce platforms, and financial accounts, from potential cyberattacks and fraud.
Lock The Vault [link]

Course: The Insider Threat: The Data Breach Is Coming From Inside - $297 - Coming Soon
Research shows that about 80% of all companies have experienced a cyberattack at least once with the top 2 major factors attributed to naive or careless mistakes by employees. With online entrepreneurs using remote teams, raising employee awareness about maintaining data security reduces that risk.
Leadership Risk Prevention Training

Course: Criming In The Age Of AI: Phishing was just the beginning - $297 - Coming Soon
ChatGPT’s own plugin red team members found they could send fraudulent or spam emails, bypass safety restrictions, or misuse information sent to the plugin, it’s time not only for a conversation about plugins, but some practical actions to keep our businesses safe.
AI Can Lie [link]

1 to 1: 90-Minute Cybersecurity Deploy/Response Training $297 - Coming Soon
From an audit to step-by-step actions, whatever you need, we'll get done.

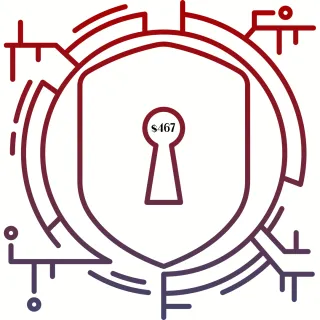
Bundle: Back That Biz Up + The Insider Threat $467 - Coming Soon
There are two things I like a lot: protecting people and a good deal. Save over 25% with a two course bundle.
Bundle: Beyond Phish Phingers + Criming In The Age Of AI $467 - Coming Soon
There are two things I like a lot: protecting people and a good deal. Save over 25% with a two course bundle.

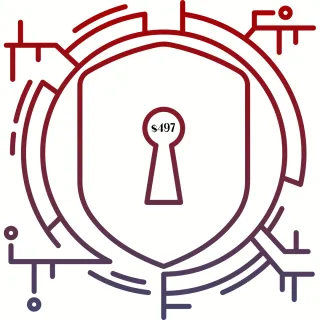
1 to 1: 3-Hour Security Help Cybersecurity Deploy/Response Training $497 - Coming Soon
When you need more than 90 minutes, but not as much as a VIP Half-Day, here's your solution.
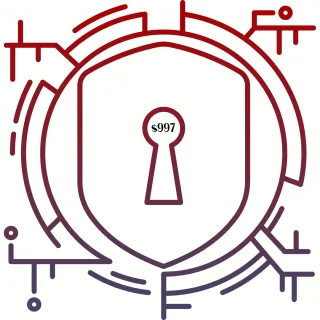
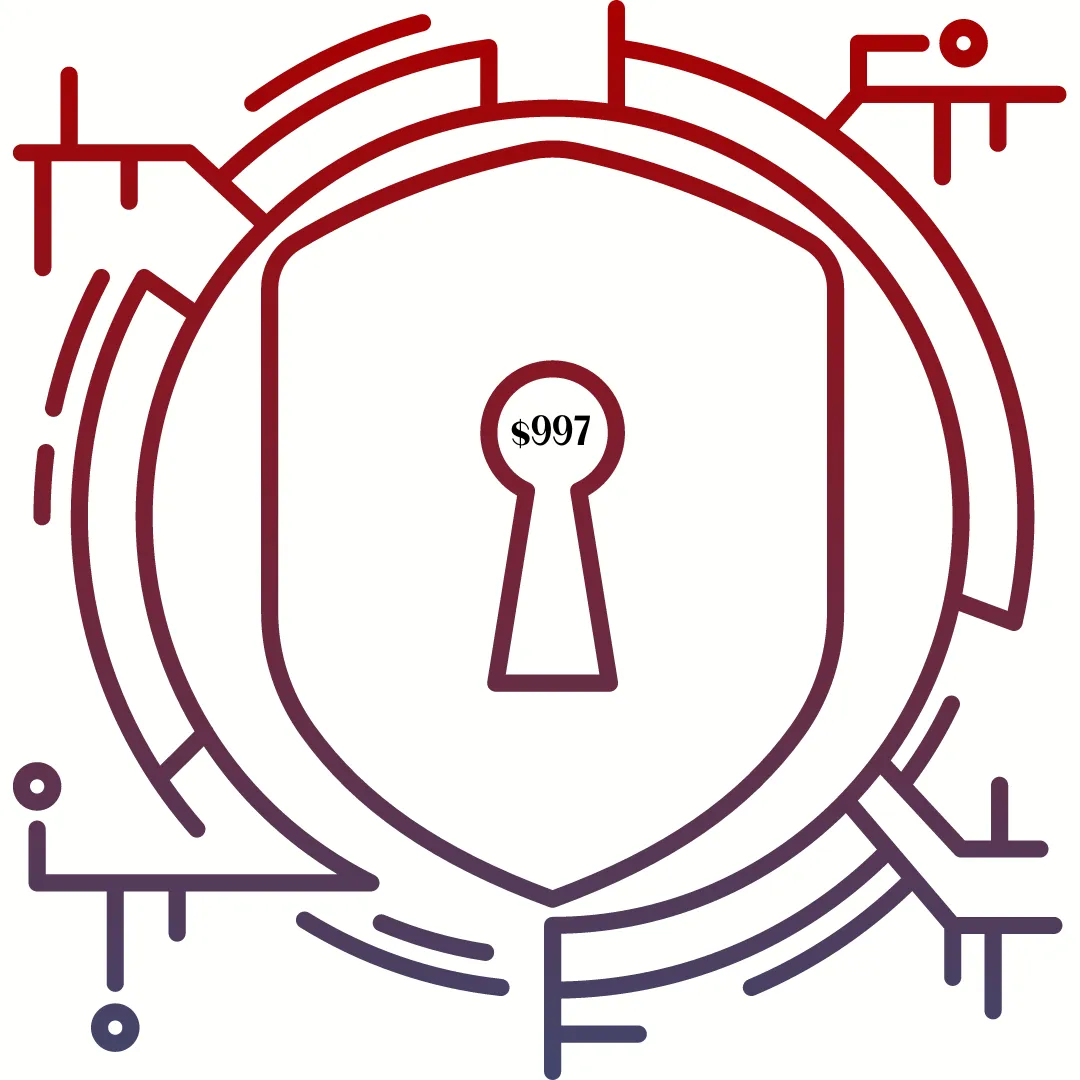
Cybersecurity Program: Creating Your Cybersecure Business Life $997 - Coming Soon
All the workshops and courses + private community + Q&A + 3 60-Minute 1:1s.
Cybersecurity + Privacy
Ghost Mode
Privacy Checklist
3rd party data collectors have massive databases worth billions. Using just a few not-the-usual-recommended techniques, you can ghost those data collectors every time you surf the web.


unAPPetizing:
What To Look For When App Updates Are Rotten.
Your mobile apps may start out passing the App Stores' stringent security vetting, but once downloaded, updates may not be safe. This cheat sheet gives all help you'll need to spot the signs of a bad app update.


Raising
CyberSmart Kids -
Quick Start Guide
As a parent, you know bad people are on the internet and you don't know what you can do about it, until now.
The Quick Start Guide to keep Kids
CyberSafe by being CyberSmart.

COMING SOON!
The Human Firewall: Strengthening Your Cybersecurity
Cybersecurity is intimidating, especially when you don't know what you don't know. We'll cover some principles, definitions, methods, and tools in this workbook to create your Cybersecurity Roadmap.


6 Ways To Say
Delete Me, Internet
As an entrepreneur, you already know your personal data is on the internet and everyone agrees there's not a thing you can do about it. But...
What if I could show you 6 ways to Say Delete me to the internet, would you be in?

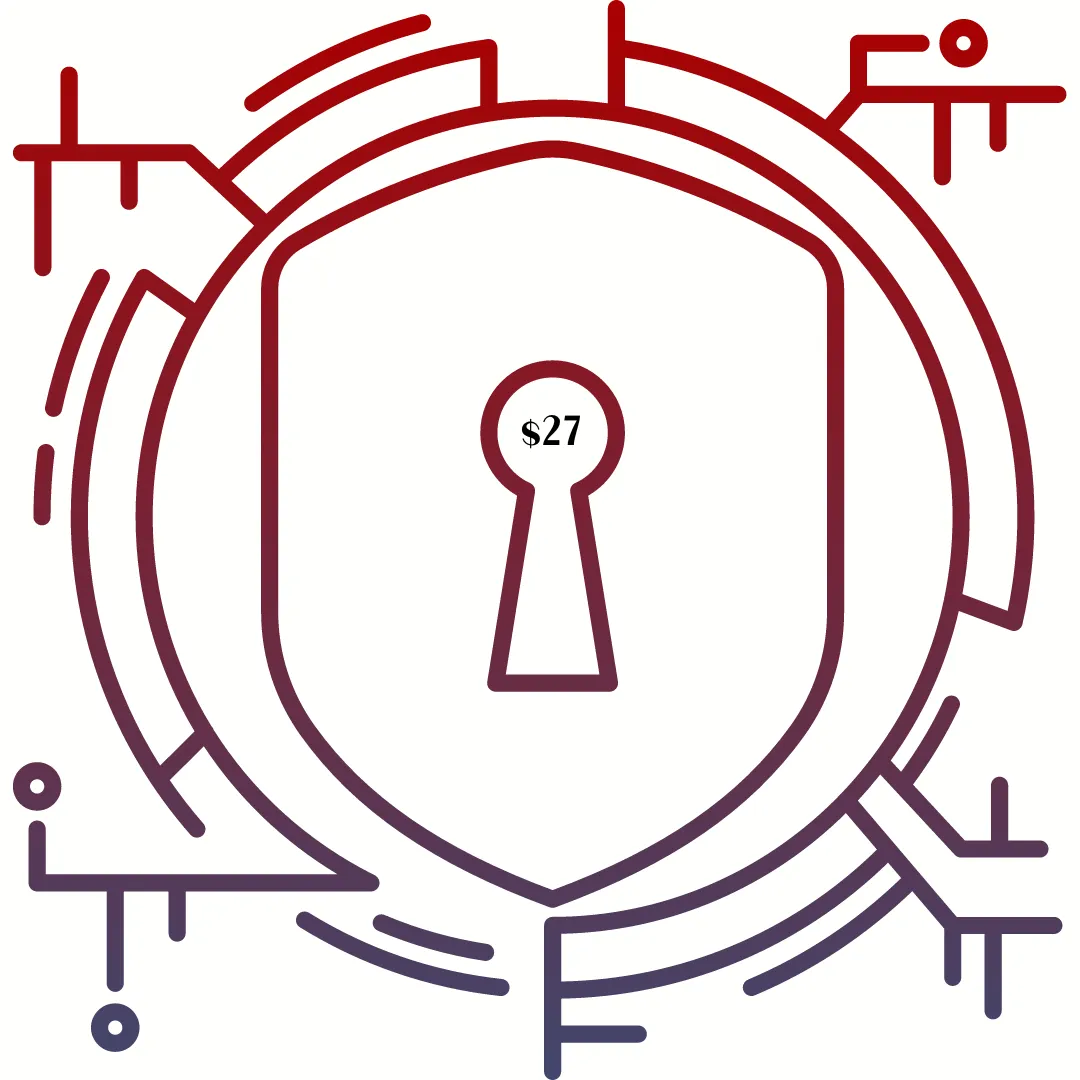
The CEO Security Brief
The Cybersecurity Subscription that breaks down complex, eyes glazed over, jargony super tech security into bite-sized, crystal clear, explain it like I’m 9 Strategies & More So Entrepreneurial CEOs Can Quickly Make Security Decisions to Protect Their Business

1:1 Help Call - 15 Minutes
This is your quick security support call. Within those 15 minutes, we'll assess an issue and determine the solution you need and how much time it will take to handle it. The call can also be used AMA style.

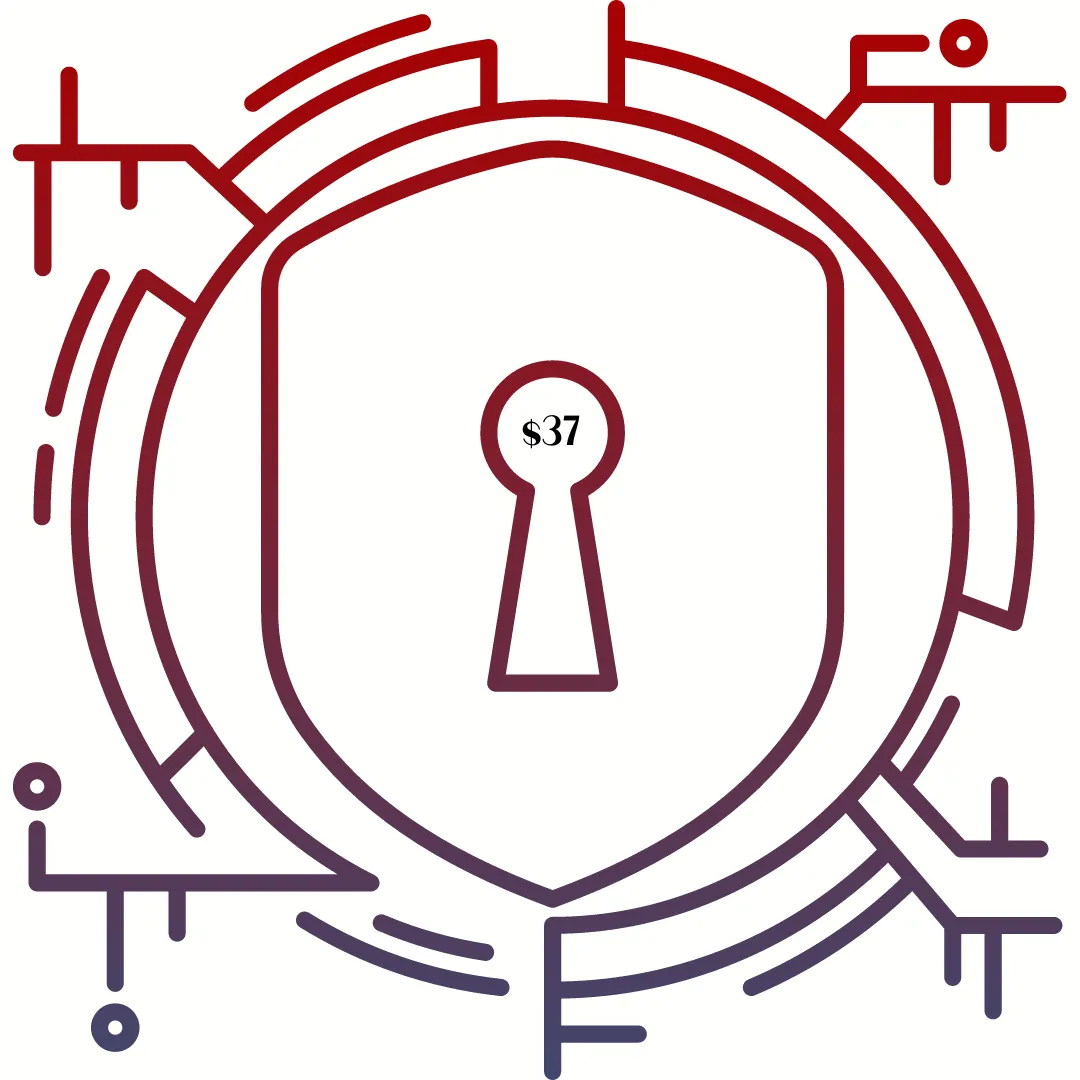
1:1 Solutions Call:
30 Minutes
This security support call is for one-to-one training, coaching, or consulting.

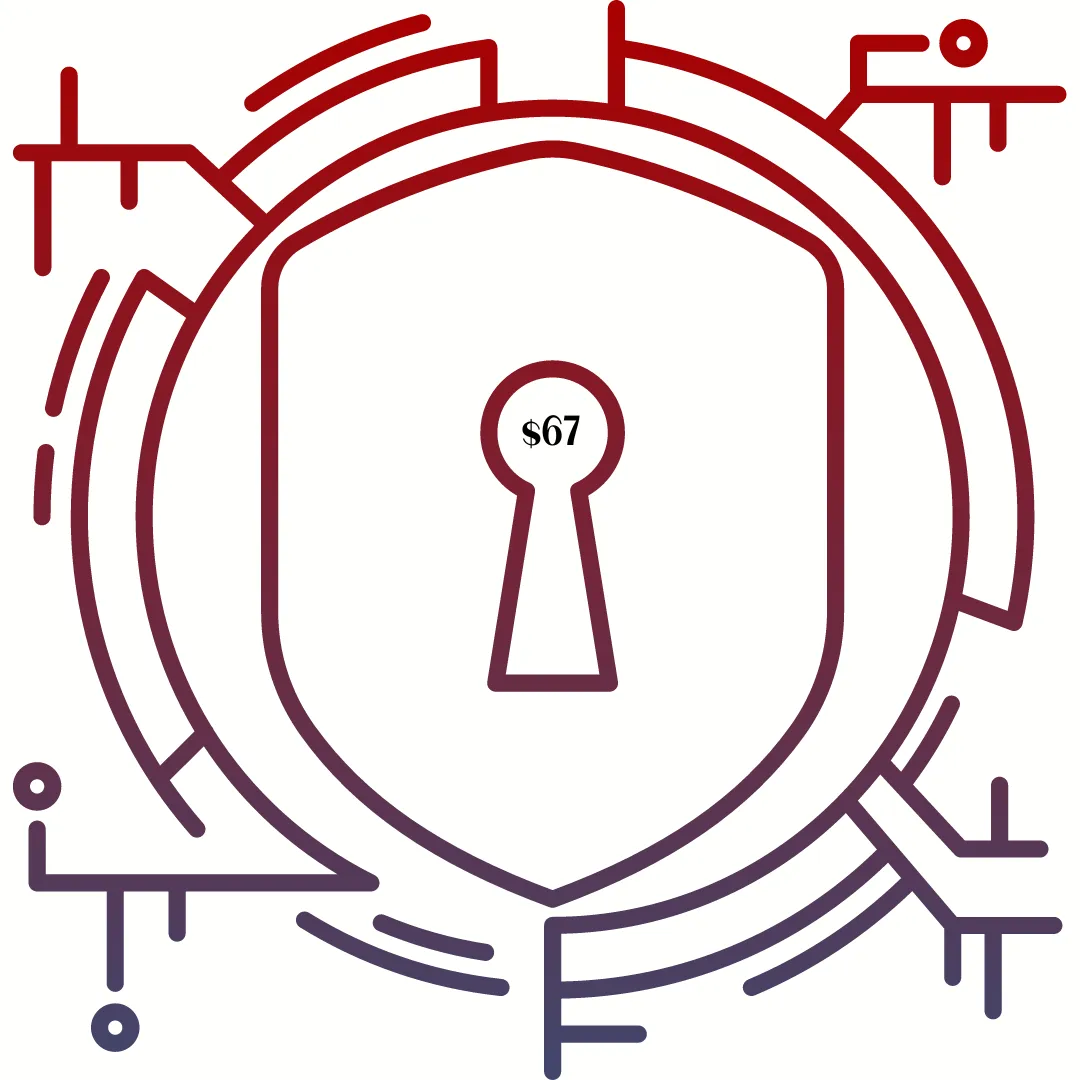
The Insider Threat: The Data Breach Is Coming From Inside
80% of all companies experienced a cyberattack with human error as the main factor. This On-Demand Workshop teaches you exactly what you need in place to protect your business.

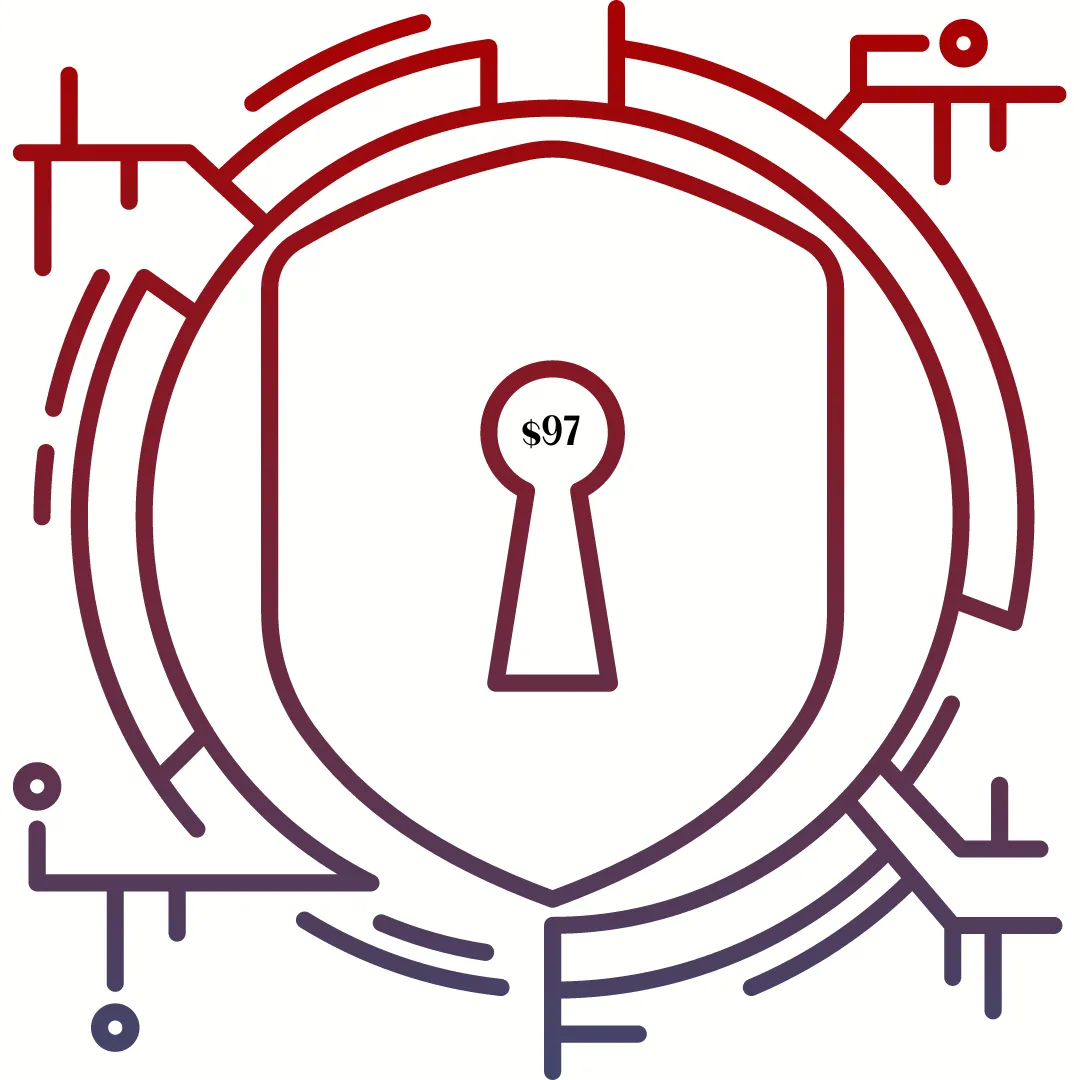
The Castle Defense Assessment Course
Discover the 6 Layers of Cybersecurity you need to keep your business secure online. From physical equipment to the human factor, you'll learn: Your current security; Its strength; what's missing; and how to get it.

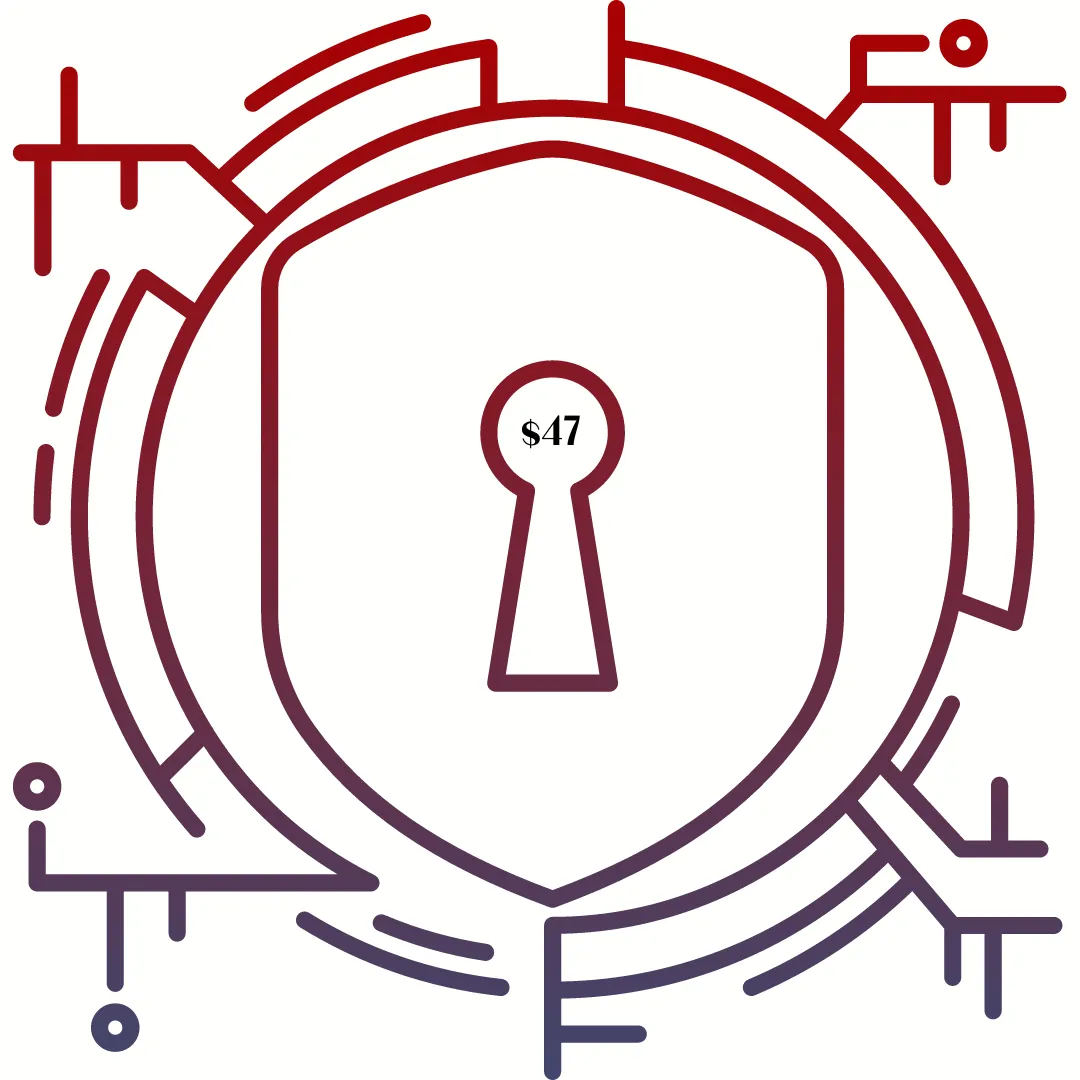
Data Defense Tactics: Protecting Your Most Valuable Asset
This LIVE workshop is the foundational first step to uncovering the fundamentals of data security and secure cloud storage.
November 28, 2023
11am PDT/2pm EDT


Mobile Mayhem: Securing Your Business on the Go
In this on-demand workshop, You'll equip yourself with the knowledge to protect your business data and communications while working remotely or traveling, ensuring that your mobile devices become impenetrable fortresses.

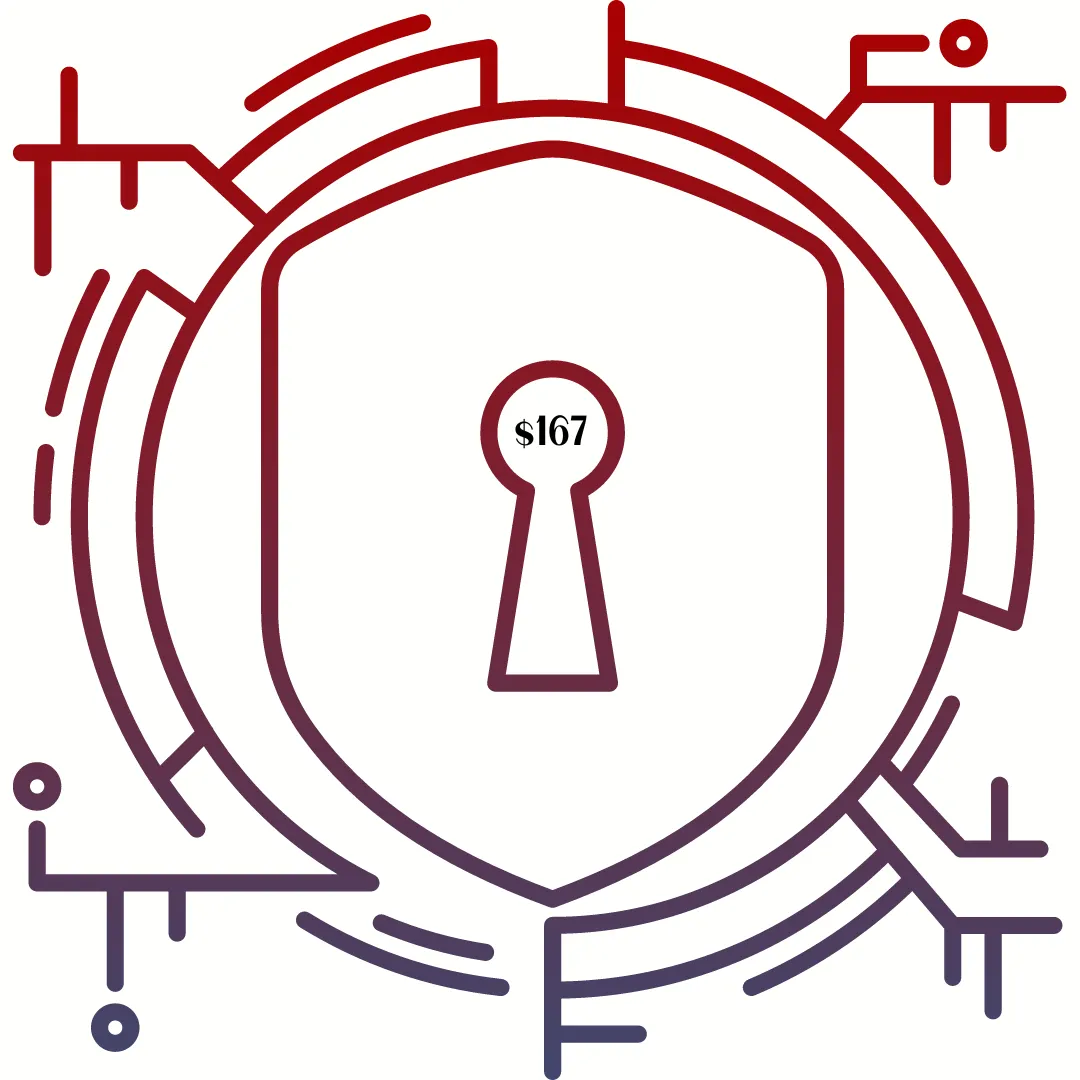
Give Phishers The Phinger: Social Media Secured
This On-Demand Workshop is your quick take action solution to Fort Knox your Facebook Account. I'll teach you how to use the best security tool and the real secret to seamless account access.


More Ways To Say Delete Me Internet
The comprehensive course to teach you how to use free and paid techniques to legally remove private information from those databases.


Small Call to Action Headline
ddddd


Small Call to Action Headline
Your Paragraph text goes Lorem ipsum dolor sit amet, consectetur adipisicing elit. Autem dolore, alias, numquam enim ab voluptate id quam harum ducimus cupiditate similique quisquam et deserunt, recusandae. here

1 to 1 VIP Security Help
BOYD: Bring Your Own Devices
Security/Privacy Audit
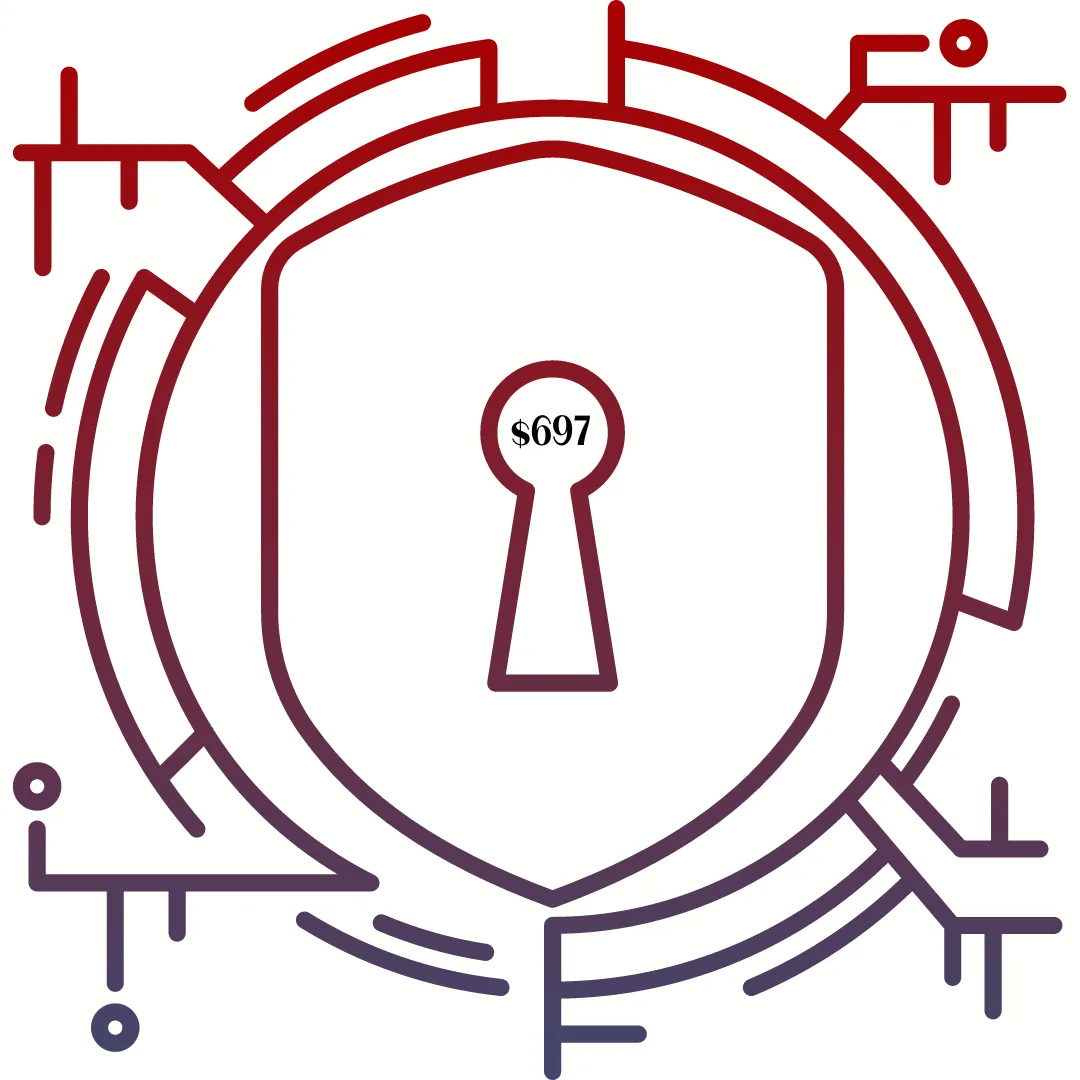
VIP Half-Day
VIP Day
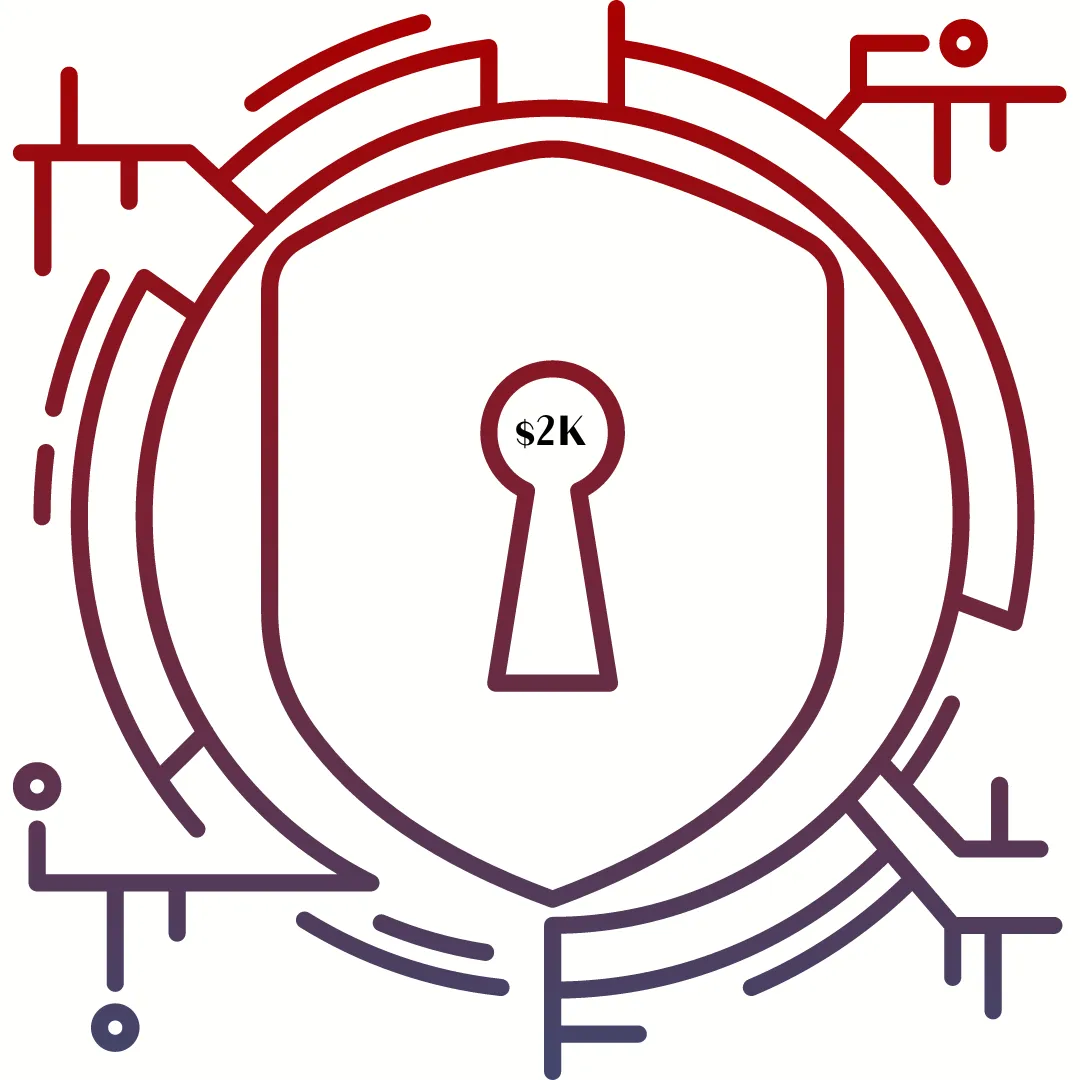
My Everything Page is so cool,
I had to share.
I just have to give a special thanks to Lizzy Goddard. Her training on something as simple as an Everything Page made all the difference as to how I can help as many people as possible.
If you want to learn more about Everything Pages...
This is my affiliate link which means I may receive a commission if you purchase something through a link at no additional cost to yourself. Please be assured that I only recommend products I have personally used and love!
The fastest way to making your business cybersafe

Cybersecurity for DIY Entrepreneur
Cybersquad security
$27/Mo
Course, Workshops, Community
Vulnerability and Protection Courses
Anti-hacker Workshops
FB Community
Checklists, Planners, plus Q&A time
02
Service Number Two
one Sentence brief description of service number one
Mauris ac vestibulum nibh, quis euismod velit. Mauris sodales tincidunt ex vitae viverra. Nunc neque eros, convallis vel eros id, molestie bibendum neque. In hac habitasse platea dictumst. Integer quis hendrerit eros tincidunt ex vitae viverra. Nunc neque eros, convallis vel eros integer quis hendrerit eros.


Service Two
$35/hr
Minimum 20 Hours Per Month
Social Media Management
WordPress Updates
FB Community Management
Graphics For Social Media Posts
SERVICE Number Three
Service THree
$35/hr
Minimum 20 Hours Per Month
Social Media Management
WordPress Updates
FB Community Management
Graphics For Social Media Posts
Lorem ipsum dolor sit amet, consectetur adipi scing elit. Aenean dolor turpis, rutrum ut velit id, volutpat tempor nibh. Sed volutpat viverra mi quis varius. Proin ultricies arcu lacus, quis ultri cies sapien venenatis sed. Praesent at lacus rutr um, ornare nisl ac, euismod nisi. Etiam cur sus varius lorem at ultricies. Sed velit eros, sodales eu tincidunt a, facilisis ac risus.



04
Service Number Four
one Sentence brief description of service number one
Mauris ac vestibulum nibh, quis euismod velit. Mauris sodales tincidunt ex vitae viverra. Nunc neque eros, convallis vel eros id, molestie bibendum neque. In hac habitasse platea dictumst. Integer quis hendrerit eros tincidunt ex vitae viverra. Nunc neque eros, convallis vel eros integer quis hendrerit eros.


Service Two
$35/hr
Minimum 20 Hours Per Month
Social Media Management
WordPress Updates
FB Community Management
Graphics For Social Media Posts
